CCNA and CCENT Tutorial: Intro To Standard ACLs
In the previous installment of this ACL tutorial series, we learned how to calculate a wildcard mask in seconds. Now we’ll take a look at the two major ACL types, starting with standard ACLs.
A standard ACL is concerned only with the source IP address of the packet. That’s literally the only value that can be configured when writing a standard ACL.
You have two numeric ranges to choose from when writing standard ACLs, and I’ve bolded those for you in this IOS Help readout. Don’t concern yourself with all of these ranges, but know the standard and extended ACL ranges by heart.
R1(config)#access-list ? <1-99> IP standard access list <100-199> IP extended access list <1000-1099> IPX SAP access list <1100-1199> Extended 48-bit MAC address access list <1200-1299> IPX summary address access list <1300-1999> IP standard access list (expanded range) <200-299> Protocol type-code access list <2000-2699> IP extended access list (expanded range) <2700-2799> MPLS access list <300-399> DECnet access list <700-799> 48-bit MAC address access list <800-899> IPX standard access list <900-999> IPX extended access list
dynamic-extended Extend the dynamic ACL absolute timer rate-limit Simple rate-limit specific access list
IOS Help will make no mention of which address you’re matching on (source or destination, that is) with a standard ACL, so we need to know it’s a source IP address. If this doesn’t come up on your exam in one way or another, I’ll grow a full head of hair.
R1(config)#access-list 5 permit ? Hostname or A.B.C.D Address to match any Any source host host A single host address
Follow the source IP with the wildcard mask, and you’re gold. Let’s write a line matching the 172.12.1.0 255.255.255.0 subnet.
R1(config)#access-list 5 permit 172.12.1.0 ? /nn or A.B.C.D Wildcard bits log Log matches against this entry <cr> R1(config)#access-list 5 permit 172.12.1.0 0.0.0.255
Some IOSes give you the choice of using the traditional dotted decimal wildcard mask or entering the mask in prefix notation. We’ll use dotted decimal here and use prefix notation in a later lab.
I want to show you the challenges that await when using standard ACLs. In this demo, R1’s Serial IP is 172.12.123.1 /24 and R3’s is 172.12.123.3 /24.
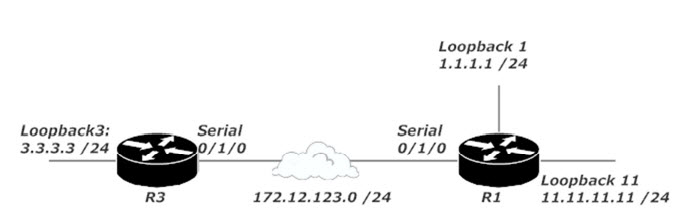
The requirements for this lab:
On R1, block traffic sourced from 3.3.3.0 /24 if it’s destined for 11.11.11.0 /24.
R1 should allow packets from 3.3.3.0 /24 if intended for any other subnet, including any subnets added in the future.
If we use a standard ACL, we can block traffic sourced from 3.3.3.0 /24 destined for 11.11.11.0 /24 with no problem. That’s the good news. The bad news is that we’ll block all traffic coming from 3.3.3.0 /24, since a standard ACL doesn’t allow us to specify the destination IP address of the packets to be blocked.
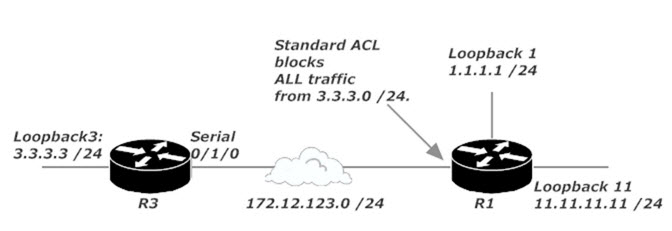
Standard ACLs can be handy for identifying traffic, but for most situations involving permitting and denying traffic, you’re better off using an extended ACL. Let’s head to the next tutorial and see what extended ACLs are all about!
Next Tutorial: Introduction To Extended ACLs
Previous Tutorial: Wildcard Masking Made Easy
First Tutorial: ACL Rules and the Implicit Deny




